As
it stands, people are forced to give out their sensitive personal data
to counterparties in a bid to identify themselves and their income
sources. This is largely because of the limitations of the
identification systems presently on ground. This leaves the data sharer
completely insecure in the event of a security rupture. It gets more
severe when an individual shares more and more personal information with
counterparties. The reason is because it becomes easier to track their
identity and their income generators.
Moreover, these counterparties frequently give out the data in their custody to third parties, either in part or in full, which further increases the vulnerability of the original data owners.
To disrupt this status quo, the IAME Identification Network emerged to alter the identification process. https://iame.io/
This modification will be such that an individual’s data will be broken up into fragments just before it is confirmed. The fragmentation will be carried out by series of autonomous third parties that are not in any way associated with any of the transactional counterparties involved in the transaction. The duty of the third parties will then be to just confirm the various fragments of the data. These fragmented data are in themselves immaterial to the third parties, and therefore cannot be utilized for fraudulent purposes.
Notwithstanding, the transactional counterparties will still have access to the complete data for valid identification, but it would be needless for the fraudulent ones to process or store non-essential data, since it will not be profitable to them.
Primarily, the IAME Identification Network is designed to serve blockchain P2P transactions, but will in the long run be extended to merchant transactions and financial institutions in the provision of blockchain related services.
The core of the IAME Identification Network would consist of – a Client, an Allocation Server, a Validation Server, a writeable blockchain and an Identity Server. Every one of these components would have a particular function to perform, and each of these functions can be manifested in two distinct but complementary processes, namely;
• Validation process
• Identification process
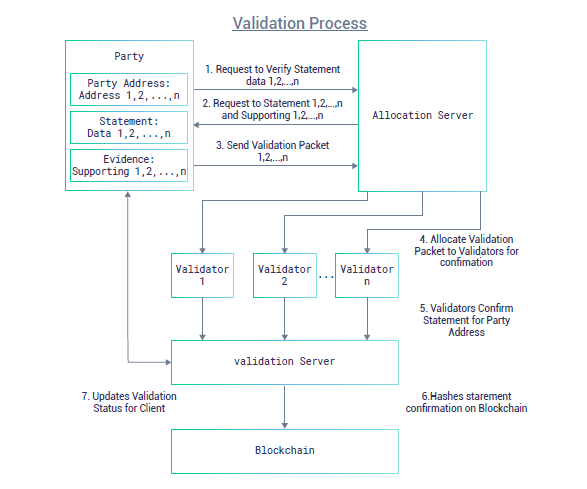
The client would have their data validated by third party validators in the validation process as shown in the sketch below.
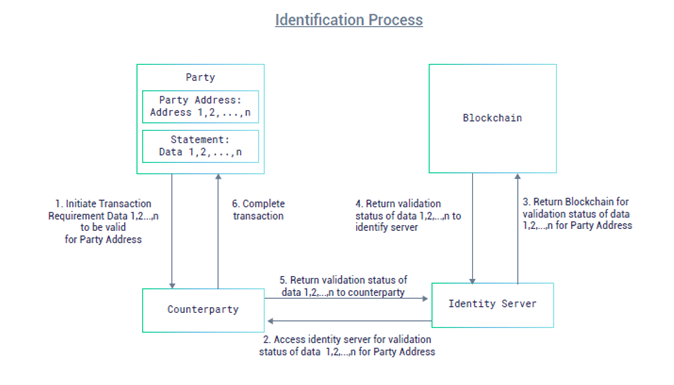
Following the validation process is the Identification process which needs to be completed to enable transaction between a counterparty and a client, strictly on the counterparty’s specified requirements. The identification process is summarized in the sketch below.
For detailed information on the IAME Identification Network, kindly download the project White Paper at https://iame.io/res/180301-IAME-White-Paper-en.pdf
An operational Token (IAM Token) will be issued by the Network. The IAM Token will serve as a validation token for the initiation of confirmation requests for validation packets on the IAME Identification Network.
The Token would be expended by parties involved in a transaction via the IAME Identification Network client. When the equivalent blockchain hashing costs has been deducted, the balance would then be paid to the third party validators as a reward.
Private sale of tokens is currently on, and will end on 5th May, 2018.
For the private sale, 1ETH = 15,000 IAM
Tokens are limited! Hurry up and buy yours now!
For more information on the Token sale, visit https://iame.io/
Stay connected with IAME on social media:
https://t.me/iame_identity
https://bitcointalk.org/index.php?topic=3218491.0
https://facebook.com/IAMEidentity
https://twitter.com/@iameidentity
https://www.linkedin.com/company/iameidentity
https://www.instagram.com/iameidentity/
https://medium.com/@IAMEIdentity
https://vimeo.com/iameidentity
Authored By : https://bitcointalk.org/index.php?action=profile;u=1165678
Moreover, these counterparties frequently give out the data in their custody to third parties, either in part or in full, which further increases the vulnerability of the original data owners.
To disrupt this status quo, the IAME Identification Network emerged to alter the identification process. https://iame.io/

This modification will be such that an individual’s data will be broken up into fragments just before it is confirmed. The fragmentation will be carried out by series of autonomous third parties that are not in any way associated with any of the transactional counterparties involved in the transaction. The duty of the third parties will then be to just confirm the various fragments of the data. These fragmented data are in themselves immaterial to the third parties, and therefore cannot be utilized for fraudulent purposes.
Notwithstanding, the transactional counterparties will still have access to the complete data for valid identification, but it would be needless for the fraudulent ones to process or store non-essential data, since it will not be profitable to them.
Primarily, the IAME Identification Network is designed to serve blockchain P2P transactions, but will in the long run be extended to merchant transactions and financial institutions in the provision of blockchain related services.
The core of the IAME Identification Network would consist of – a Client, an Allocation Server, a Validation Server, a writeable blockchain and an Identity Server. Every one of these components would have a particular function to perform, and each of these functions can be manifested in two distinct but complementary processes, namely;
• Validation process
• Identification process
The client would have their data validated by third party validators in the validation process as shown in the sketch below.

Following the validation process is the Identification process which needs to be completed to enable transaction between a counterparty and a client, strictly on the counterparty’s specified requirements. The identification process is summarized in the sketch below.

For detailed information on the IAME Identification Network, kindly download the project White Paper at https://iame.io/res/180301-IAME-White-Paper-en.pdf
An operational Token (IAM Token) will be issued by the Network. The IAM Token will serve as a validation token for the initiation of confirmation requests for validation packets on the IAME Identification Network.
The Token would be expended by parties involved in a transaction via the IAME Identification Network client. When the equivalent blockchain hashing costs has been deducted, the balance would then be paid to the third party validators as a reward.
Private sale of tokens is currently on, and will end on 5th May, 2018.
For the private sale, 1ETH = 15,000 IAM
Tokens are limited! Hurry up and buy yours now!
For more information on the Token sale, visit https://iame.io/
Stay connected with IAME on social media:
https://t.me/iame_identity
https://bitcointalk.org/index.php?topic=3218491.0
https://facebook.com/IAMEidentity
https://twitter.com/@iameidentity
https://www.linkedin.com/company/iameidentity
https://www.instagram.com/iameidentity/
https://medium.com/@IAMEIdentity
https://vimeo.com/iameidentity
Authored By : https://bitcointalk.org/index.php?action=profile;u=1165678
Comments
Post a Comment